What is Symlink?
A symlink (also called a symbolic link) is a type of file that points to another file or a folder on your computer. Symlinks are similar to shortcuts in Windows or alias in Mac but it is not an actual file. Symbolic links are supported by Mac, Windows, and Unix, but are most commonly found on Unix systems since Unix is known for having a large (and often confusing) hierarchy of directories. If you delete the soft link, nothing will happen to the file but if the original file is deleted the soft link fails.
What Is the Symlink Attack?
Symlink bugs are vulnerabilities that may allow an attacker to overwrite certain or even arbitrary files with the permissions of the invoking user of the vulnerable application or script. The typical symlink bug allows one to overwrite or corrupt files not usually accessible to themselves or could otherwise trick the vulnerable application or script to write to a *critical* system file which could possibly leave the host OS inoperable. This symlink vulnerability allows a malicious user to serve files from anywhere on a server that has not been protected by strict OS-level permissions.
Preventing Symlink Attack
- Installation of CageFS: CloudLinux
CageFS is a virtualized file system and a set of tools to contain each user in its own ‘cage’. This option is available on all cPanel-supported platforms today, and it is already included with CloudLinux.
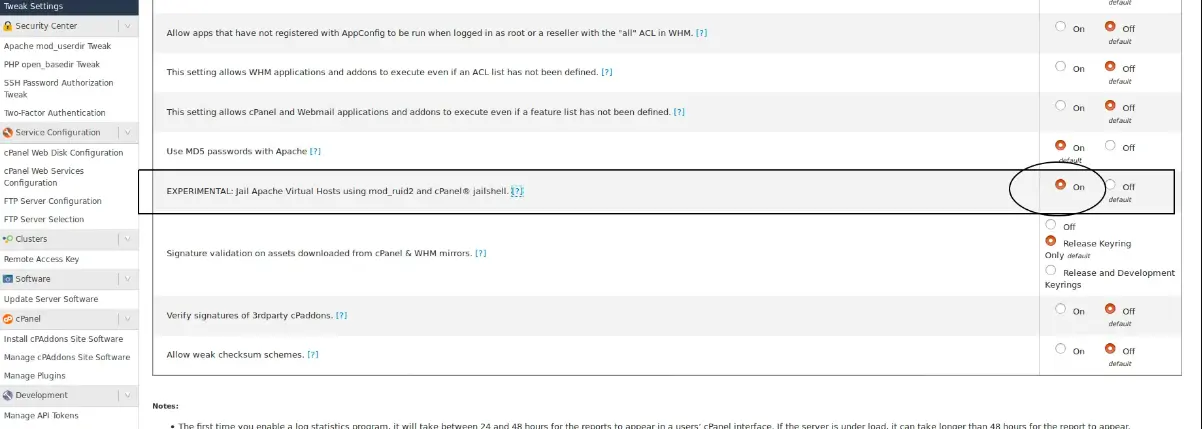
CloudLinux is integrated with Apache (suexec, suPHP, mod_fcgid, mod_fastcgi) . This is a core feature that will help you to avoid symlink attacks. - Jail Apache Virtual Hosts Via mod_ruid2 and cPanel Jailshell
When you enable this option from the security tab from the WHM then, this action will run Apache virtual hosts in a chrooted environment. You can enable this from WHM’s Tweak Settings interface.
WHM >> Server Configuration >> Tweak Settings

- CloudLinux SecureLinks
CloudLinux SecureLinks is a safe option to address race condition vulnerability. This option prevents symlink attacks at the kernel level. CloudLinux installs this option by default, but it does not affect virtual hosts that do not specify a user ID. - GRSec kernel patch
The GRSec kernel patch provides a safe option to address the race condition vulnerability.This patch provides kernel-level protection against race conditions. However, to use it, you must use a custom kernel, which requires additional installation and maintenance. - Apache-level patches
To use the symlink protection patch, select On for the Symlink Protection option in the Global Configuration section of WHM configuration interface (WHM >> Home >> Service Configuration >> Apache Configuration >> Global Configuration).
To enable the patch manually, set the following:

Warning:
EasyApache 4 does not apply this patch by default.
This patch may slow the performance of high-traffic servers.
If you already use a custom patch for the race condition (such as the FollowSymLinks_to_OwnerMatch.patch), you must either remove your custom patch or not enable the Symlink Protection option.



Leave A Comment